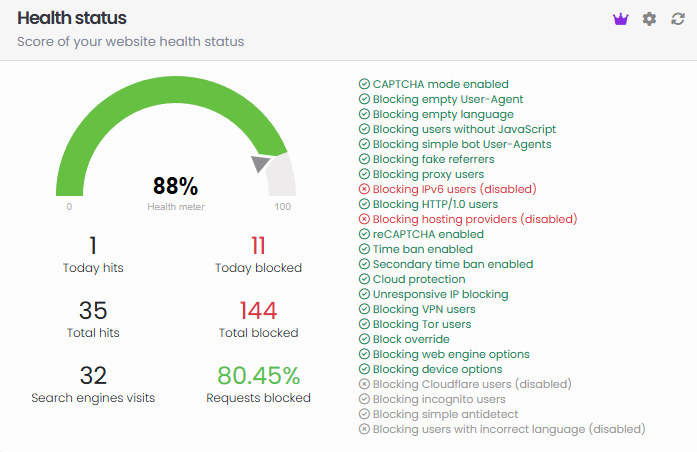
The BotBlocker plugin is designed to detect, analyze, and block malicious or unwanted bot traffic while minimizing interruptions for legitimate users. To achieve this, it implements a structured, multi-layered process for filtering requests. Below is a detailed explanation of its functionality, focusing on the logical flow of operations:
1. Initial Preparations
Before analyzing the incoming request, the plugin initializes key parameters and configurations:
- Session Initialization: A unique session identifier is generated for tracking the request.
- Request Metadata Collection: Basic information such as the request timestamp, client IP address, protocol, headers, and User-Agent is captured. These details form the foundation for subsequent checks.
- Preliminary Configuration: The plugin verifies that critical components, such as error headers and cryptographic salt files, are in place to ensure smooth operation. If these are missing, they are generated dynamically.
This stage ensures that the environment is ready for advanced analysis.
2. Quick Exclusions
To save resources, the plugin immediately excludes certain types of requests:
- System-Level Traffic: Requests generated by server-side processes (e.g., WordPress CRON jobs) are identified and excluded from further processing. These are considered safe by default.
- Whitelisted IPs: If the incoming request originates from an IP address explicitly marked as trusted (e.g., administrators), it is bypassed.
These quick checks reduce unnecessary computations for known, legitimate traffic.
3. Comprehensive Data Collection
For requests that are not excluded, the plugin gathers detailed information:
- Client Information: Data such as the client’s browser, operating system, and device type are determined by analyzing the User-Agent string.
- Network Attributes: The plugin evaluates the IP address to determine its version (IPv4 or IPv6), geographical location, associated Autonomous System Number (ASN), and whether the IP belongs to a hosting provider or is part of a known proxy.
- Request Headers: Specific headers, including those related to language preferences, accepted content types, and referer, are examined to assess the legitimacy of the request.
- Protocol Checks: It analyzes the HTTP protocol version to identify outdated or non-standard usage (e.g., HTTP/1.0).
- Behavioral Patterns: The plugin evaluates the presence and validity of cookies, tracking request frequency, and identifying anomalies.
This comprehensive profiling enables a deeper understanding of the request context.
4. Cloud-Based Enrichment
For enhanced accuracy, the plugin leverages external APIs to gather supplementary data about the client’s IP address:
- Geolocation: The client’s country and associated CIDR range are identified.
- Hosting Detection: Indicators such as whether the IP address belongs to a hosting provider are retrieved. This helps identify potential threats from data centers often used by bots.
- Reputation Data: Additional information about the IP’s reputation or history of malicious activity may also be fetched.
- Proxy Detection: Cloud data enhances the identification of proxies or VPNs, which might indicate suspicious activity.
This stage adds valuable context for distinguishing between legitimate and suspicious traffic.
5. Behavioral and Rule-Based Analysis
The plugin then analyzes the behavior and attributes of the request against defined rules:
- User-Agent Validation: It matches the User-Agent against predefined lists of known bots or good bots (e.g., search engine crawlers). Fake or generic User-Agent strings are flagged.
- Header and Cookie Validation: Requests with missing or malformed headers, such as empty User-Agent strings, invalid language settings, or absent cookies, are scrutinized.
- IP-Based Rules: The client’s IP is checked against extensive lists of blacklisted, whitelisted, or graylisted ranges. Temporary bans for expired rules are automatically removed.
- Referer Analysis: The referer header is analyzed for consistency with the request’s context. Fake referers or those with inconsistent structures are flagged as suspicious.
- Rate Limiting: Using cookies, the plugin tracks request frequency per user. If the request count exceeds predefined thresholds, the user is blocked.
- Language-Country Mismatch: Requests where the language does not align with the detected country are flagged as potentially malicious.
- Behavioral Patterns: It tracks user interaction patterns, such as browsing behavior and access type, identifying anomalies or suspicious activity.
- Hosting and Proxy Detection: IPs identified as belonging to hosting providers or known proxies are treated with caution and possibly blocked.
- Protocol and Path Checks: The plugin evaluates HTTP protocols and inspects request paths for matches against known attack patterns or malicious behavior.
These rules allow the plugin to pinpoint and classify various threat levels accurately.
6. Decision Tree Execution
The plugin uses the aggregated information to make a final determination about the request:
- Allow: Requests identified as legitimate are passed through without additional interference. Cookies may be set to streamline future interactions.
- Block: Malicious or clearly harmful requests are immediately blocked, with the user receiving a custom error page or an appropriate HTTP status code.
- Challenge: For ambiguous cases, the plugin may present a CAPTCHA or other verification mechanism to confirm the legitimacy of the user.
- Graylisting: Suspect requests are temporarily allowed but monitored closely for further actions.
This structured decision-making process ensures that each request is handled appropriately based on its risk profile.
7. Logging and Reporting
Regardless of the outcome, the plugin maintains detailed logs:
- Blocked Requests: Comprehensive data on blocked requests, including the IP, User-Agent, headers, and reason for blocking, is stored for future reference.
- Allowed Requests: Even allowed requests are logged to monitor trends, identify false positives, and refine rules.
- Rule Application: Each applied rule and its result are recorded for transparency and debugging purposes.
Logs enable administrators to analyze traffic, understand attack patterns, and adjust rules as necessary.
8. Periodic Maintenance and Updates
The plugin incorporates mechanisms to stay up-to-date:
- Rule Updates: Regular updates to blacklists, whitelists, and heuristic rules ensure the plugin remains effective against emerging threats.
- Geolocation Data: Frequent updates to geolocation databases ensure accurate identification of IP attributes.
- Behavioral Thresholds: Thresholds for rate limiting, request validation, and behavioral checks are periodically reviewed and adjusted based on traffic trends.
This maintenance ensures the plugin’s continued reliability and effectiveness in mitigating threats.
By incorporating an extensive range of checks and leveraging both local and cloud-based data, the BotBlocker plugin ensures comprehensive protection against bot traffic. Its multi-layered approach, combined with efficient logging and regular updates, provides robust site security while maintaining minimal impact on legitimate users.